Introduction to Cybersecurity
talks
This is a presentation for introducing new people to cybersecurity.
Below is the same presentation, rendered to html with the slide titles as headers.
If you want to see the presentation in slides form, click the “RevealJS” format on the right, under “Other formats”.
OSI Model and Our Name
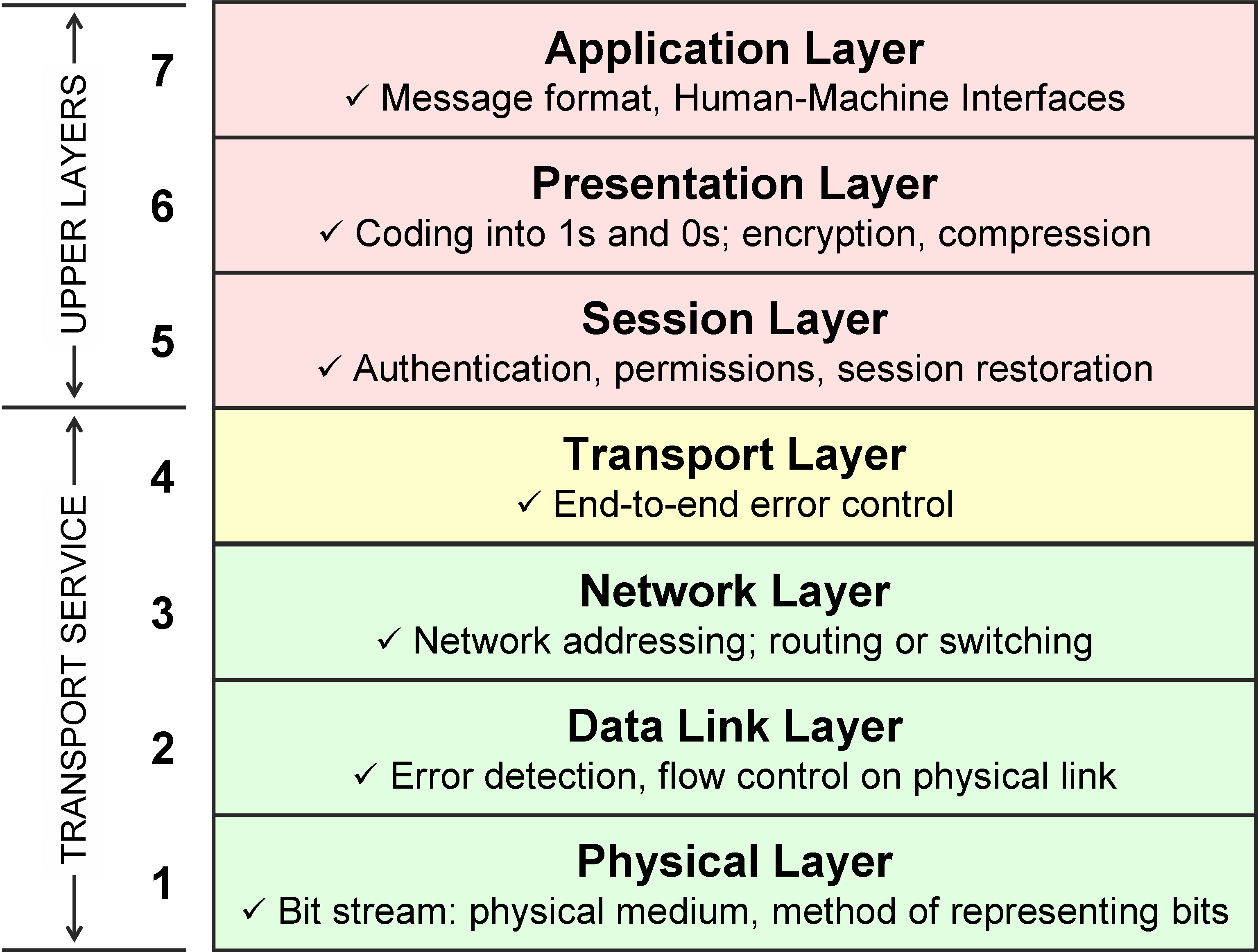
Cybersecurity is:
- Methods used to secure systems from malice or human error
- Backups!
Types of Machines
- Servers: Run things like web pages or game servers
- Desktops: Machines you normally interact with
Common Methodologies for Servers
- Limit services in use (attack surface)
- “Harden” services
- “Agent” software, which monitors systems
Methodologies for Desktops
- Restrict downloading of software
- “Agent” software to monitor systems
- Education of users
Operating Systems
- Windows, Linux, and Mac
- Windows and Mac are common for desktops
- Linux is common for servers
Overthewire Bandit
- https://overthewire.org/wargames/bandit/
- Good place to get started for Linux related things
- All answers to the challenges can be found in the built in documentation accessible via the
mancommand.
Web Based Terminals:
Interesting Youtubers
- SoBatistaCyber’s Overthewire walkthrough
- Please don’t use this…
- LaurieWired
Futher Resources
- https://www.womeninlinux.org/
- There is a big conference called SCaLE, which happens yearly in March